Create Ingress with IP Allowlisting
This uses beta features in the platform and breaking changes may occur in the future
Create middleware
If on your resource you come across a middleware.traefik.containo.us, that is an older version of Treaefik’s CRD. It
will be deprecated in the future.
Create a middleware.traefik.io object to allowlist IP addresses :
apiVersion: traefik.io/v1alpha1
kind: Middleware
metadata:
name: <middlewareName>
namespace: <middlewareNamespace>
spec:
ipAllowList:
ipStrategy:
depth: 2 # request is forwarded from load balancer (X-Forwarded-For). Depth is counted from the right.
sourceRange:
- <ip-address>
- <ip-address>Use Middleware in Ingress
Reference middleware in our Ingress object with the annotation traefik.ingress.kubernetes.io/router.middlewares: <middlewareNamespace>-<middlewareName>@kubernetescrd, for example:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
labels:
annotations:
external-dns.alpha.kubernetes.io/hostname: foo.gcp-dev.cecg.platform.cecg.io # change this to point to your hostname
external-dns.alpha.kubernetes.io/target: gcp-dev.cecg.platform.cecg.io # change this to point to your domain
traefik.ingress.kubernetes.io/router.middlewares: <middlewareNamespace>-<middlewareName>@kubernetescrd
name: foo-app
namespace: foo
spec:
ingressClassName: platform-ingress
rules:
- host: foo.gcp-dev.cecg.platform.cecg.io
http:
paths:
- backend:
service:
name: foo-service
port:
number: 80
path: /
pathType: ImplementationSpecificAfter you apply this, only users with allowlisted IPs will be able to use that ingress URL.
Debugging
Dashboard
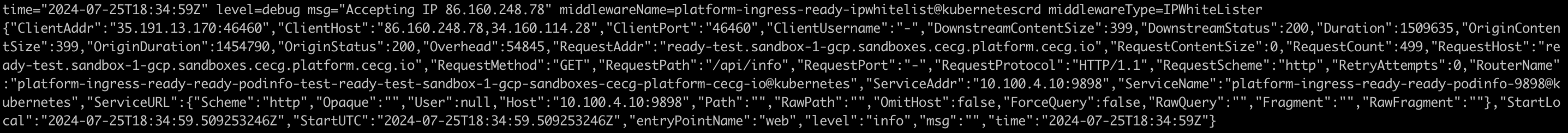
To validate that your Middleware has been applied successfully, check the Traefik Dashboard and ensure that it contains no errors.
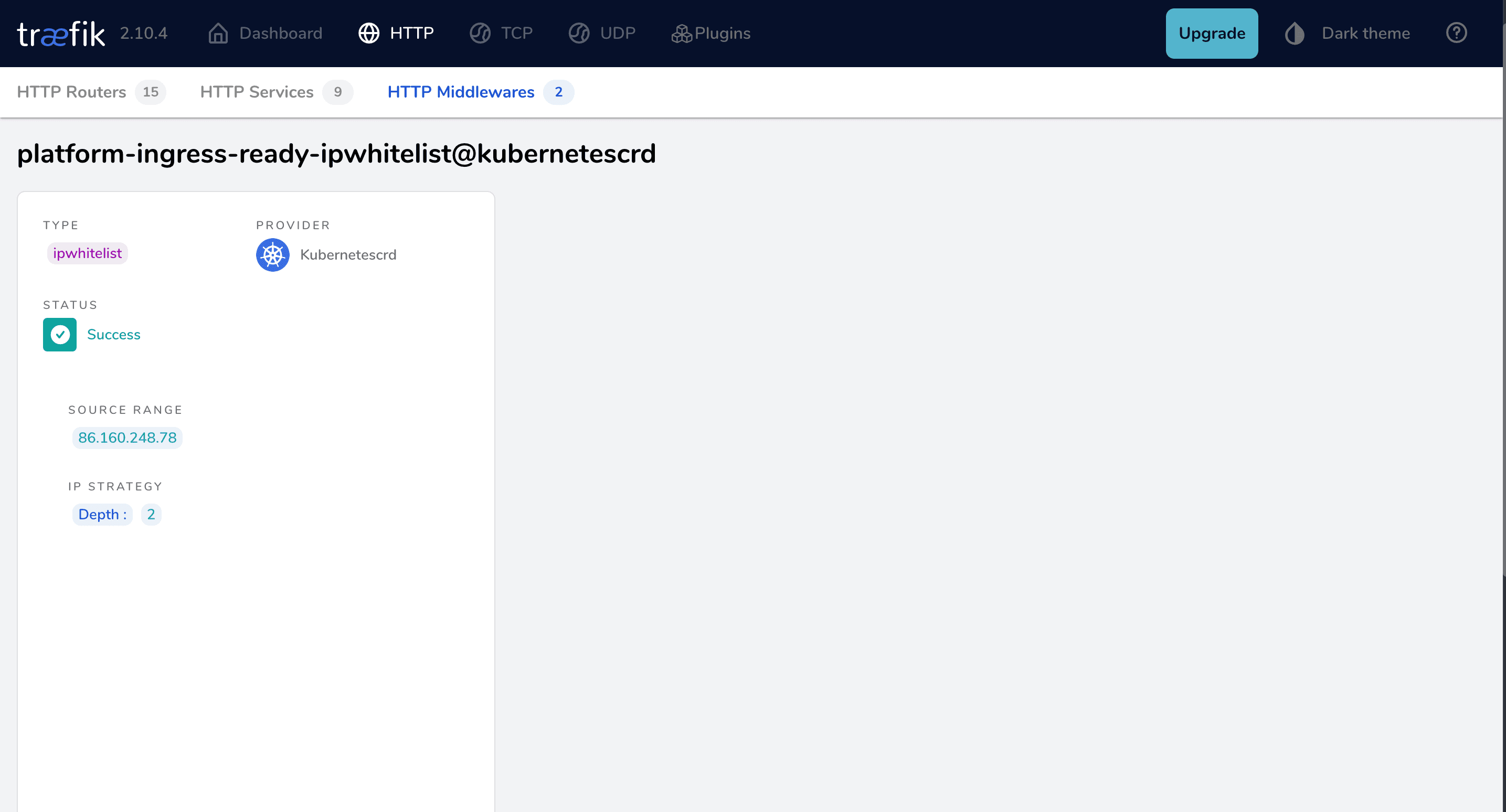
Logs
Check traefik logs to see whether request is being allowlisted: